| Here is the spam millions of netizens found in their mailboxes... |
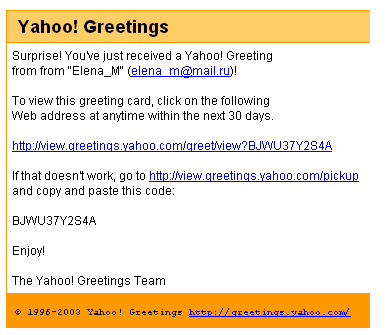
Attempts
to view the card did lead (depending on your browser security configuration)
to the following offer for a screensaver from the http://view-greetings-yahoo.com
site: |
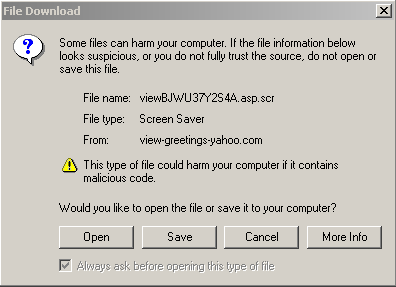
Basic Analysis Obviously somethings is fishy here: well behaved greeting cards do not aspire to camp on one's hard drive. The attentive reader will also have noticed that the effective url, view-greetings-yahoo.com differs markedly from the initial view.greetings.yahoo.com... but how many average netizens pay attention to those details? Besides, even if they bother to check the web server at view-greetings-yahoo.com they risk being deceived as it looks exactly as the main Yahoo! server at view.greetings.yahoo.com. We decided to investigate this "greeting card" further and downloaded the alleged screen saver. Once run, it simply displays the following message: Error on line 25: invalid object An average user would dismiss the message and forget about it. Behind the scene however, another program called sysman32.exe has been downloaded and is ready to run at the next reboot. Sysman32.exe aims where it hurts: at the user's wallet. Active in memory, it monitors the web browser windows and attempts to steal the credentials the user uses to access his webmoney wallet, his paypal account, his "Gold" accounts (whatever that means) or, in a generic way, the passwords the user uses to access the pages where he "signs-in". When its fishing expedition pays off, the trojan e-mails its bounty home. More specifically, the trojan
|